Author:
Durga Prasada Rao SanaganaPublished in
Journal of Science Technology and Research( Volume , Issue )
1. Prasad, B. S., Gupta, S., Borah, N., Dineshkumar, R., Lautre, H. K., & Mouleswararao, B. (2023). Predicting diabetes with multivariate analysis an innovative KNN-based classifier approach. Preventive Medicine, 174, 107619.
2. Prasad, B. V. V. S., and Sheba Angel. “Predicting future resource requirement for efficient resource management in cloud.” International Journal of Computer Applications 101, no. 15 (2014): 19-23.
3. Prasad, B. V., and S. Salman Ali. “Software–defined networking based secure rout-ing in mobile ad hoc network.” International Journal of Engineering & Technology 7.1.2 (2017): 229.
4. Alapati, N., Prasad, B. V. V. S., Sharma, A., Kumari, G. R. P., Veeneetha, S. V., Srivalli, N., … & Sahitya, D. (2022, November). Prediction of Flight-fare using machine learning. In 2022 International Conference on Fourth Industrial Revolution Based Technology and Practices (ICFIRTP) (pp. 134-138). IEEE.
5. Kumar, B. R., Ashok, G., & Prasad, B. S. (2015). Tuning PID Controller Parameters for Load Frequency Control Considering System Uncertainties. Int. Journal of Engineering Research and Applications, 5(5), 42-47.
6. Ali, S. S., & Prasad, B. V. V. S. (2017). Secure and energy aware routing protocol (SEARP) based on trust-factor in Mobile Ad-Hoc networks. Journal of Statistics and Management Systems, 20(4), 543–551. https://doi.org/10.1080/09720510.2017.1395174
7. Onyema, E. M., Balasubaramanian, S., Iwendi, C., Prasad, B. S., & Edeh, C. D. (2023). Remote monitoring system using slow-fast deep convolution neural network model for identifying anti-social activities in surveillance applications. Measurement: Sensors, 27, 100718.
8. Syed, S. A., & Prasad, B. V. V. S. (2019, April). Merged technique to prevent SYBIL Attacks in VANETs. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-6). IEEE.
9. Patil, P. D., & Chavan, N. (2014). Proximate analysis and mineral characterization of Barringtonia species. International Journal of Advances in Pharmaceutical Analysis, 4(3), 120-122.
10. Desai, Mrunalini N., Priya D. Patil, and N. S. Chavan. “ISOLATION AND CHARACTERIZATION OF STARCH FROM MANGROVES Aegiceras corniculatum (L.) Blanco and Cynometra iripa Kostel.” (2011).
11. Patil, P. D., Gokhale, M. V., & Chavan, N. S. (2014). Mango starch: Its use and future prospects. Innov. J. Food Sci, 2, 29-30.
12. Priya Patil, D., N. S. Chavan, and B. S. Anjali. “Sonneratia alba J. Smith, A Vital Source of Gamma Linolenic Acid (GLA).” Asian J Pharm Clin Res 5.1 (2012): 172-175.
13. Priya, D., Patil, A., Niranjana, S., & Chavan, A. (2012). Potential testing of fatty acids from mangrove Aegiceras corniculatum (L.) Blanco. Int J Pharm Sci, 3, 569-71.
14. Priya, D., Patil, A., Niranjana, S., & Chavan, A. (2012). Potential testing of fatty acids from mangrove Aegiceras corniculatum (L.) Blanco. Int J Pharm Sci, 3, 569-71.
15. Patil, Priya D., and N. S. Chavan. “A comparative study of nutrients and mineral composition of Carallia brachiata (Lour.) Merill.” International Journal of Advanced Science and Research 1 (2015): 90-92.
16. Patil, P. D., & Chavan, N. S. (2013). A need of conservation of Bruguiera species as a famine food. Annals Food Science and Technology, 14, 294-297.
17. Bharathi, G. P., Chandra, I., Sanagana, D. P. R., Tummalachervu, C. K., Rao, V. S., &Neelima, S. (2024). AI-driven adaptive learning for enhancing business intelligence simulation games. Entertainment Computing, 50, 100699.
18. Nagarani, N., et al. “Self-attention based progressive generative adversarial network optimized with momentum search optimization algorithm for classification of brain tumor on MRI image.” Biomedical Signal Processing and Control 88 (2024): 105597.
19. Reka, R., R. Karthick, R. Saravana Ram, and Gurkirpal Singh. “Multi head self-attention gated graph convolutional network based multi‑attack intrusion detection in MANET.” Computers & Security 136 (2024): 103526.
20. Meenalochini, P., R. Karthick, and E. Sakthivel. “An Efficient Control Strategy for an Extended Switched Coupled Inductor Quasi-Z-Source Inverter for 3 Φ Grid Connected System.” Journal of Circuits, Systems and Computers 32.11 (2023): 2450011.
21. Karthick, R., et al. “An optimal partitioning and floor planning for VLSI circuit design based on a hybrid bio-inspired whale optimization and adaptive bird swarm optimization (WO-ABSO) algorithm.” Journal of Circuits, Systems and Computers 32.08 (2023): 2350273.
22. Jasper Gnana Chandran, J., et al. “Dual-channel capsule generative adversarial network optimized with golden eagle optimization for pediatric bone age assessment from hand X-ray image.” International Journal of Pattern Recognition and Artificial Intelligence 37.02 (2023): 2354001.
23. Rajagopal RK, Karthick R, Meenalochini P, Kalaichelvi T. Deep Convolutional Spiking Neural Network optimized with Arithmetic optimization algorithm for lung disease detection using chest X-ray images. Biomedical Signal Processing and Control. 2023 Jan 1;79:104197.
24. Karthick, R., and P. Meenalochini. “Implementation of data cache block (DCB) in shared processor using field-programmable gate array (FPGA).” Journal of the National Science Foundation of Sri Lanka 48.4 (2020).
25. Karthick, R., A. Senthilselvi, P. Meenalochini, and S. Senthil Pandi. “Design and analysis of linear phase finite impulse response filter using water strider optimization algorithm in FPGA.” Circuits, Systems, and Signal Processing 41, no. 9 (2022): 5254-5282.
26. Kanth, T. C. (2024). AI-POWERED THREAT INTELLIGENCE FOR PROACTIVE SECURITY MONITORING IN CLOUD INFRASTRUCTURES.
27. Karthick, R., and M. Sundararajan. “SPIDER-based out-of-order execution scheme for HtMPSOC.” International Journal of Advanced Intelligence paradigms 19.1 (2021): 28-41.
28. Karthick, R., Dawood, M.S. & Meenalochini, P. Analysis of vital signs using remote photoplethysmography (RPPG). J Ambient Intell Human Comput 14, 16729–16736 (2023). https://doi.org/10.1007/s12652-023-04683-w
29. Selvan, M. A., & Amali, S. M. J. (2024). RAINFALL DETECTION USING DEEP LEARNING TECHNIQUE
ABSTRACT:
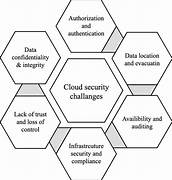
Preventing insider threats in cloud environments is crucial as traditional security systems often fail to detect internal risks. This study investigates how anomaly detection and behavioral analysis can strengthen cloud security frameworks. We examine the core challenges posed by cloud infrastructure, especially when authorized users unintentionally or maliciously compromise sensitive systems. By evaluating current threat detection techniques and integrating behavior-based monitoring, we demonstrate effective methods for enhancing data protection. Anomaly detection highlights irregular access patterns, while behavioral analysis tracks deviations in user behavior. When combined, these strategies offer a proactive defense mechanism against insider threats. Our findings emphasize that a layered security approach—tailored to the decentralized and scalable nature of the cloud—can mitigate internal vulnerabilities. As organizations increasingly rely on cloud technologies, implementing intelligent detection systems becomes essential. This research offers practical insights into preventing insider threats in cloud environments, promoting data integrity, compliance, and operational resilience.
INTRODUCTION:
As cloud adoption accelerates, preventing insider threats in cloud environments has become a top security priority. While cloud computing enables scalability, cost-efficiency, and flexibility, it also presents complex security challenges. Insider threats—stemming from authorized users misusing access, whether accidentally or intentionally—are particularly difficult to detect in cloud settings. Traditional on-premises security solutions often lack the visibility and adaptability needed for dynamic, multi-tenant cloud platforms. Additionally, the shared responsibility model complicates accountability between service providers and users. This paper explores how combining anomaly detection with behavioral analysis can mitigate insider threats effectively. Anomaly detection identifies suspicious deviations in activity, while behavioral analysis tracks user intent and usage trends. These techniques enable real-time monitoring and rapid response, essential for securing cloud infrastructure. By adopting these advanced methods, organizations can safeguard critical data, reduce risk exposure, and maintain trust. This introduction frames our comprehensive examination of proactive strategies for preventing insider threats in cloud environments.